Full system VPN-style tunneling using v2rayN, Shadowsocks, and Sing-box TUN mode.
This project provides a hardened Bash script to enforce persistent, secure DNS configuration on Ubuntu VPS systems hosted on IONOS.
Key improvement vs v2: DHCP is still used for IP/gateway, but DHCP-provided DNS (IONOS 212.227.x.x) is ignored — see technical discussion.
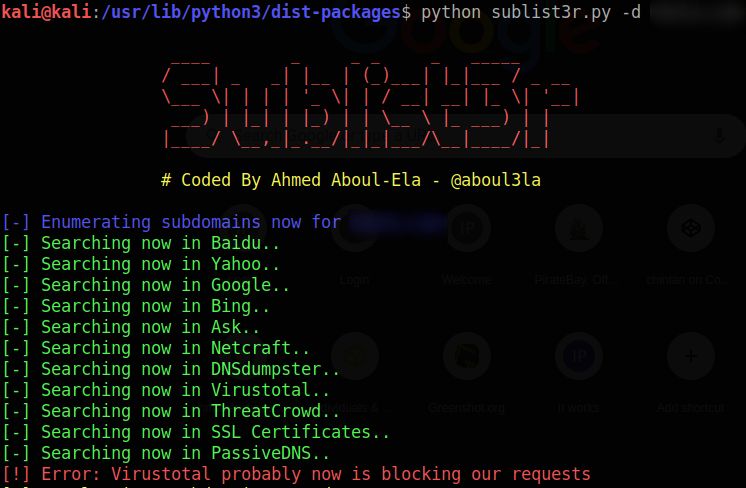
Sublist3r is a Python tool designed to enumerate subdomains of websites using OSINT. It helps penetration testers and bug hunters collect and gather subdomains for the domain they are targeting. Sublist3r enumerates subdomains using many search engines such as Google, Yahoo, Bing, Baidu, and Ask. Sublist3r also enumerates subdomains using Netcraft, Virustotal, ThreatCrowd, DNSdumpster, and ReverseDNS.
subbrute was integrated with Sublist3r to increase the possibility of finding more subdomains using bruteforce with an improved wordlist. The credit goes to TheRook who is the author of the subbrute.
This document explains how to install, run, and clean up Sublist3r when it is installed directly from the official GitHub repository.
This repository provides a PowerShell script that automatically downloads, configures, and launches the RustDesk Windows x64 portable client, using only your self-hosted ID server and public key.
It is ideal for:
- 🔧 Mass deployment (RMM, GPO, Intune, etc.)
- 🧰 Technicians who need a ready-to-use portable RustDesk client
- 💼 Environments where software installation is restricted
Note
| <# | |
| RustDesk Portable (x64) Auto Downloader & Configurator | |
| ----------------------------------------------------- | |
| • Downloads the latest available RustDesk Windows x64 portable client from GitHub | |
| • No installation (single .exe) | |
| • Automatically sets: | |
| - ID server | |
| - Key | |
| (Relay e API non impostati) | |
| • Creates and updates a download log |
In multi-user environments, providing controlled access to file transfer services is a recurring requirement. This document describes a structured procedure for configuring a non-privileged user account on Ubuntu 22.04.5 with access restricted exclusively to SFTP. Additionally, it outlines the optional configuration of reverse TCP tunneling over SSH, intended for controlled administrative or connectivity use cases. The configuration ensures compliance with security best practices by removing administrative privileges,
Hash functions are ubiquitous in information security: they are used for integrity checks, content-addressed storage, digital signatures, password verification, and more. This document treats three families of constructions that have received the most attention in practice and in the literature: MD5 (an historical design of the MD family), SHA-2 (notably SHA-256, standardized in FIPS 180), and SHA-3 (the Keccak-based family standardized in FIPS 202). Where necessary we contrast the design principles (MerkleDamgrd vs. sponge) and explain the consequences for security. Key primary sources are cited: the MD5 specification (RFC 1321), the SHA standards (FIPS 180-4), the SHA-3 standard (FIPS 202), and major cryptanalytic work on MD5 and related constructions. citeturn0search0turn0search7turn3search2
Let (H:{0,1}^* o{0,1}^n) be a deterministic function mapping binary strings of arbitrary length to fixed-length (n)-bit o
Database normalization is a fundamental methodology in relational database design. Its main objectives are:
- Reduce redundancy
- Prevent anomalies
- Maintain data integrity
This document provides an overview of the six normal forms, including BCNF, with practical examples.