User's Hypixel and Discord buttons are not correctly escaped/sanitized before they become part of the string that is inserted with innerHTML (which is a bad idea), allowing the injection of malicious attributes/events into the anchor tag (Hypixel button), the tag could not be closed because the function htmlEntities encodes these characters /[\u00A0-\u9999<>\&]/g.
HTML Injection is possible for the Discord button, but it's only possible to insert harmless tags.
It's probably possible to exploit CSS Injection and/or others attacks but I could not confirm due to Hypixel's character limitation.
Vulnerability description from OWASP
Stored XSS occurs when a web application gathers input from a user which might be malicious, and then stores that input in a data store for later use. The input that is stored is not correctly filtered. As a consequence, the malicious data will appear to be part of the web site and run within the user’s browser under the privileges of the web application. Since this vulnerability typically involves at least two requests to the application, this may also called second-order XSS.
| Affected domain | Severity | Weakness | Reported | Resolved |
|---|---|---|---|---|
| https://mcuserna.me | Medium | Cross Site Scripting (XSS) | 09/14/2022, 05:25am UTC-3 | 09/14/2022, 11:44am UTC-3 |
Someone with bad intentions could entirely change the layout of the site, make http requests, display nsfw content, use it as a tracker or ip-grabber etc...
- Join mc server
hypixel.net - Type
/profileon chat - Select
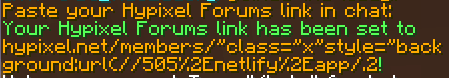
Social Media->Hypixel Forums - Paste payload on chat:
hypixel.net/members/"onmouseover="alert()//.0 - Open your mcun profile, hover over hypixel button and voilà!
encoded . = %2E
They strangely accepts inputs like in this regex:
^(https?\:\/\/)?hypixel\.net\/members\/[^.]*\.\d+$
I haven't tried to inject more than 222 characters
but the payload can probably be longer than that.
mcusername_xss_poc.mp4
The Hypixel user-controlled input should be encoded with the js function encodeURI before being inserted into the href.
The Discord user-controlled input should be encoded with the already created js function htmlEntities.
Read more about xss prevention here
old wrong suggestion
This suggested function would solve the xss bug, but would have formed invalid links.
For now, replace the current htmlEntities function with this new one with another regex, and use it in all user-controlled inputs:
function htmlEntities(str){
return String(str).replace(/[^\w. ]/gi, function(c){
return '&#'+c.charCodeAt(0)+';';
});
}Read more about xss prevention here (the above code is taken from there, but the safest and most preventive idea would be to use a framework with pre-defined functions like these that would do the job automatically).
- Minecraft UUID:
02e1d6772d0f4121b01533c3e143686f - Discord:
Slowftw#0550
- https://gist.github.com/lucky-swede/96229d2262e48fe8e41c1a251ea29770
- https://benhoyt.com/writings/dont-sanitize-do-escape
- https://owasp.org/www-community/attacks/xss/#stored-xss-attacks
- https://portswigger.net/web-security/cross-site-scripting/stored
- https://portswigger.net/web-security/cross-site-scripting/preventing
- CWE-20: Improper Input Validation
- CWE-83: Improper Neutralization of Script in Attributes in a Web Page
- CWE-116: Improper Encoding or Escaping of Output
Date: 09/14/2022, 11:44am UTC-3
- The flaw has been fixed by using DOMPurify on the string that is inserted with the innerHTML function, which at first solved the XSS but was not enough to prevent further exploits, you can read more about this here: https://gist.github.com/Slowftw/c872da1cf8611b8095b9e77b56dc5d11