This document outlines how to model a common organization-based permission system in Hasura. Let's assume that you have some table structure like the following:
| Table Name | Columns | Foreign Keys |
|---|---|---|
| User | id, name, email | |
| Organization User | id, user_id, organization_id | user_id -> user.id, organization_id -> organization.id |
| Organization | id, name |
Here we have example users, two (John and Jane) belonging to Organization ID 1, and Frank belonging to Organization ID 2:
| User | Organization User | Organization |
|---|---|---|
 |
 |
 |
We create the following relationships on our data:
| User | Organization User | Organization |
|---|---|---|
 |
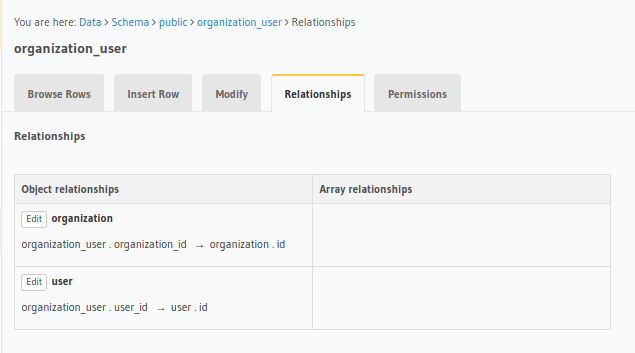 |
 |
And provision the permissions like such:
| User | Organization User | Organization |
|---|---|---|
 |
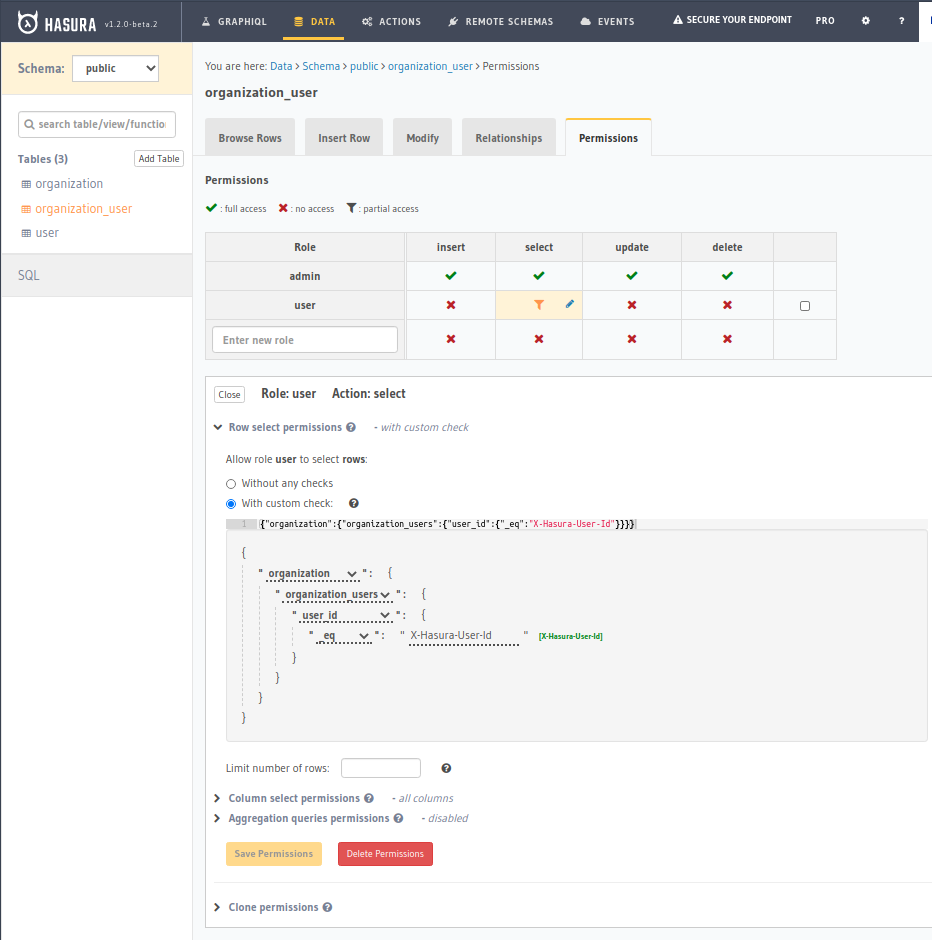 |
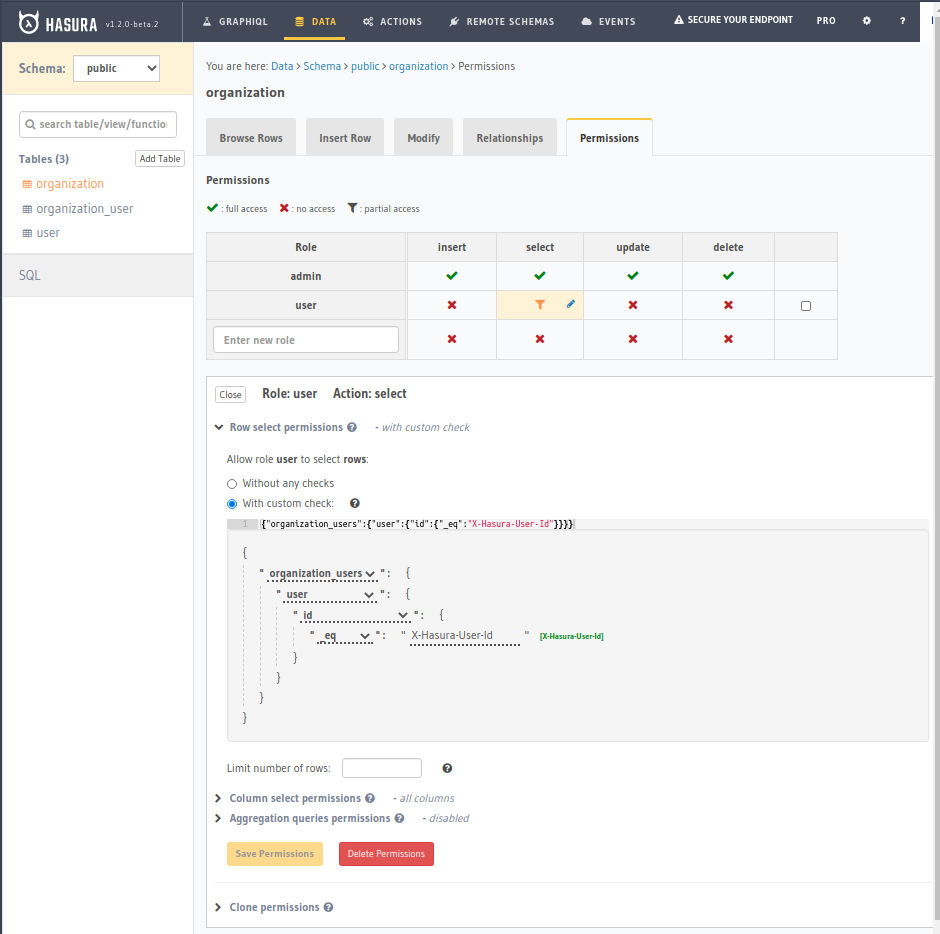 |
Now when we query with our X-Hasura-User-Id set as User 1 and 3 respectively, we can see only those users in our own organizations:
| User ID 1 (Org 1) | User ID 3 (Org 2) |
|---|---|
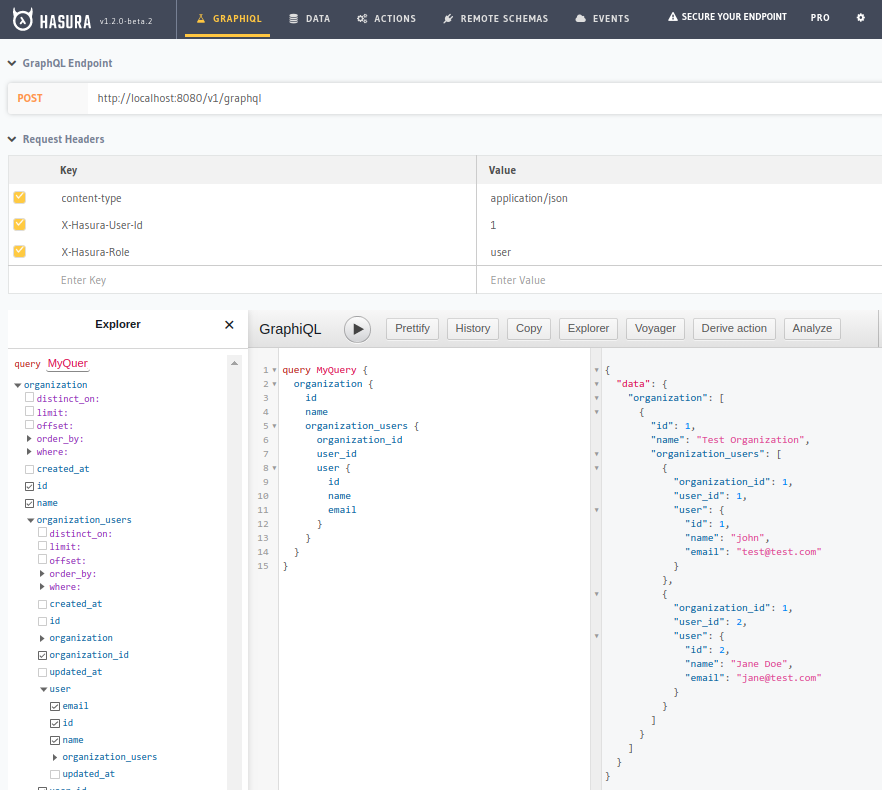 |
 |

@sidespin-admin This works fairly well for most applications where's there a concept of "groups", "teams", "tenents", or "organizations".
If you ignore the table names, the premise is:
So if your domain model has this requirement, you can probably adapt some version of this for your needs 👍